The big picture
I always like to start with the big picture—security teams are responsible for protecting their company from any adversary who may breach their network, steal data, or prevent ransomware or any other outage.
In large organizations, the security teams are divided into different teams, where SOC and threat-hunting are part of the Security Operation. Of course, these teams are not responsible for all the security aspects of their organization.
The primary role of a SOC is continuous TDIR – threat detection, investigation, and response.
These are some bad results for SOC operations:
- Too many false positives - overwhelming your SOC operation.
- Blind spots - not having the data or skillset to detect specific attacks.
- Repetitive TDIR cases - waste of time and resources.
- Long time for TDIR - too much time spent for each incident.
The root causes of these issues are generally either technology limitations or a lack of resources like people or skills. The first priority of any security team is not getting breached, but if you have too many false positives or blind spots, and if it takes you hours to investigate an incident, then you’ll get hacked, and none of the KPIs and metrics really matter.
Defenders are still heavily focused on compliance and frameworks, where real-life adversaries couldn’t care less. They need one success to evade your protection, and usually, they don’t mind spending months being stealthy. They are a profit-oriented business operating globally in many different networks at the same time.
Why do we need metrics?
The main reason for having metrics in any field is getting better. Using historical data benchmarks, you should constantly know where and when you have poor results, which would make your team and their performance better. If you are creating metrics only to get a nice dashboard of numbers, to impress yourself, to get a promotion, and to be compliance-oriented, then you are doing it for the wrong reasons.
Vanity metrics appear impressive but provide little actual value in assessing security effectiveness. They often focus on quantity over quality and can mislead about the true state of security.
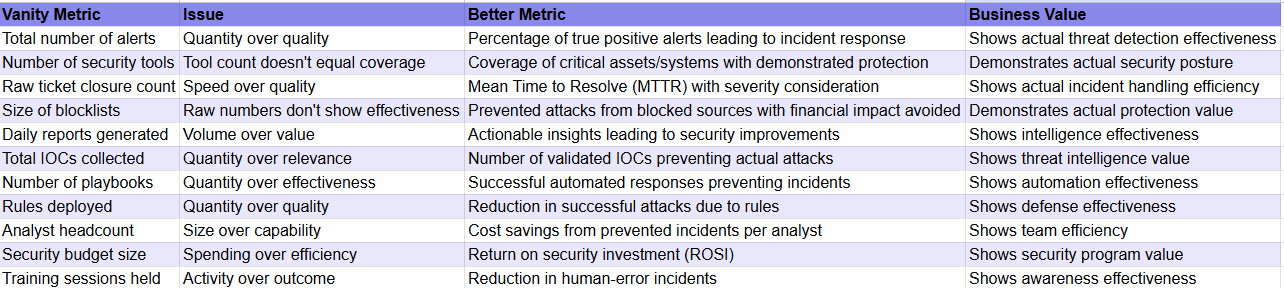
Which metrics, then?
MTTD and MTTR, for example, can be measured only for the attacks you know about, but if you don’t have time to investigate FP/TP very quickly, or if you have a large gap of blind spots, then you would never know the real MTTD/R.
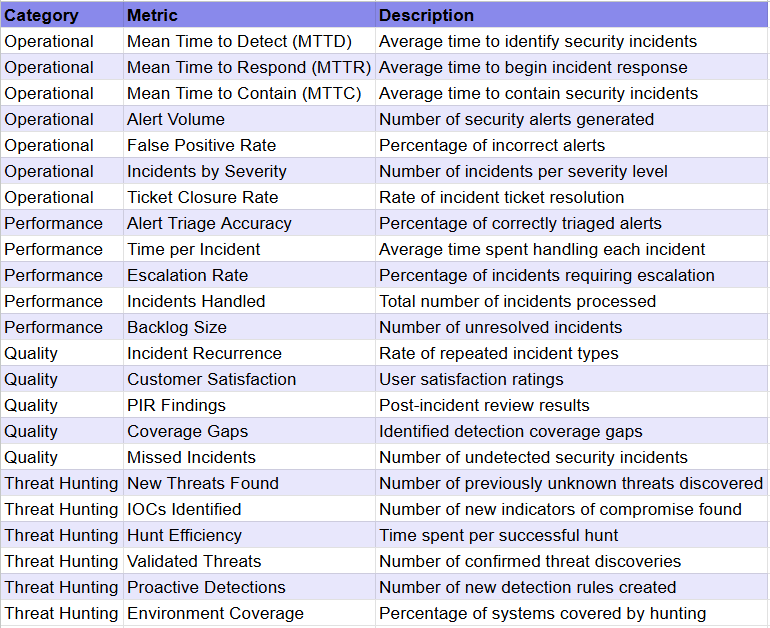
Conclusion
There’s no “one-size-fits-all,” of course, but the extreme case of measuring nothing is a terrible practice, and having the wrong metrics for your organization will also lead to bad results.
Effective SOC metrics should drive meaningful security improvements rather than just looking good in reports. Focus on measurements that help identify gaps, improve detection and response capabilities, and reduce actual risk to the business. Regularly reviewing and adjusting metrics ensures they remain relevant to evolving threats and business needs. The goal isn’t to have perfect metrics but to have metrics that help you defend better against real threats. Continuously evaluate whether your measurements drive the right behaviors and improvements in your security operations.